MANAGED SECURITY SERVICES
Managed Security Services Dubai
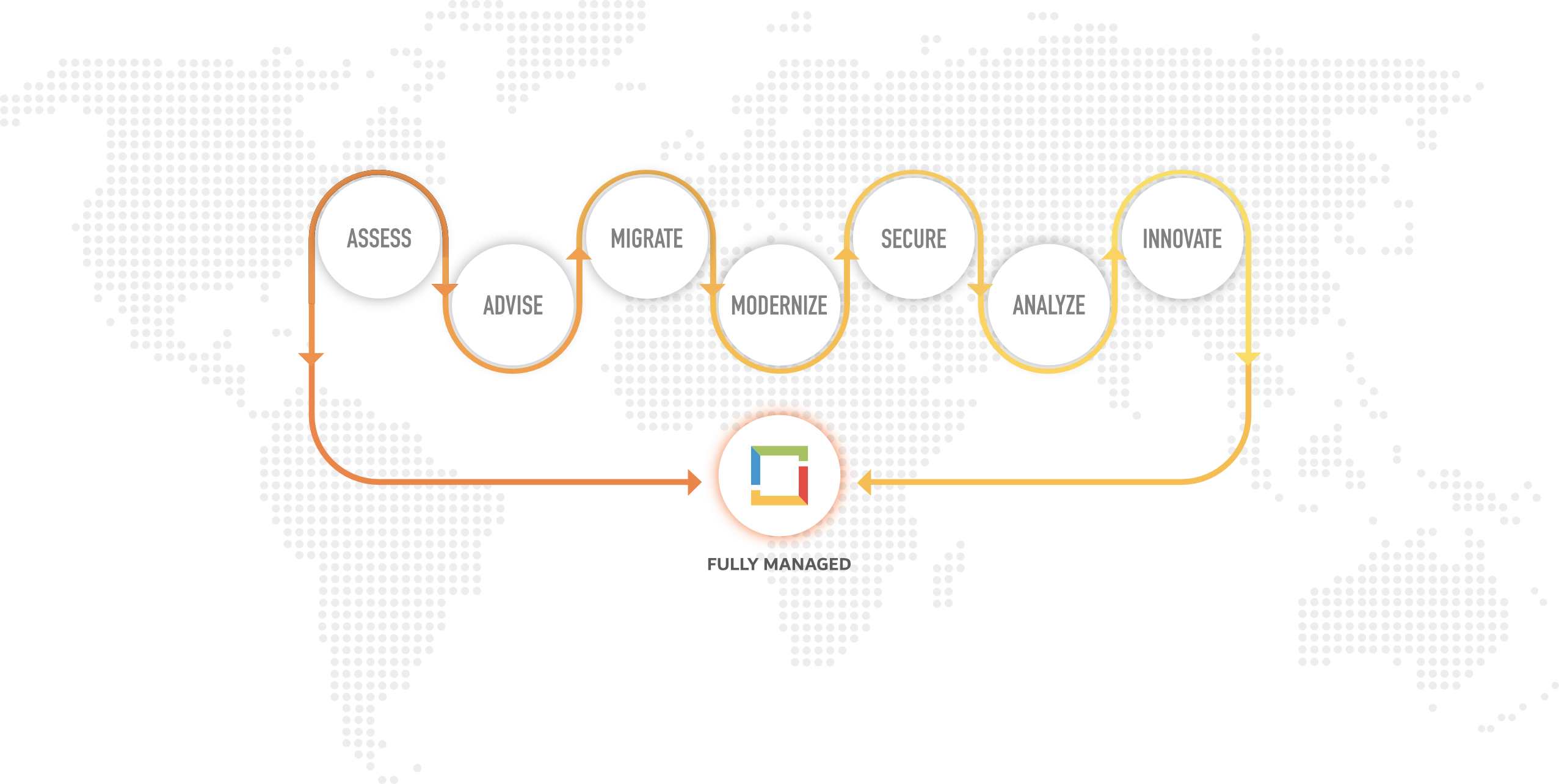
Whether you are looking to invest in new security technologies to better protect your organisation or need assistance managing and monitoring existing systems, Burhani’s extensive security expertise and knowledge of how to get the most from the latest tools means we are best placed to support your needs. Discover our range of managed security services.
Burhani Managed Services is one of the top Managed IT Services Dubai.
Our extensive experience conducting offensive security services like pen testing and red teaming means we have first-hand knowledge of the latest adversarial techniques, and we use this insight to better defend our managed security service clients against new and emerging threats.
We provide a wide range of Managed IT Security Services for businesses located in Dubai & across the UAE. Many businesses choose to switch their IT to us to reap our high customer service levels.
Helping Organizations Prevent, Detect, and Respond to Evolving Threats
Unmatched, fully managed security, identity, and compliance solutions for your business in the cloud and on premises

CYBERSECURITY SERVICES
The Comprehensive Approach to Cyber Confidence
Maximise security investments and reduce the burden of technology management by outsourcing your needs to a dedicated team of specialists.

Device Security
Protect your devices from the latest threats and stop cyber criminals gaining access to your sensitive data.
Learn More
An abundance of sensitive data will be stored on and transferred between your devices (laptops, smartphones, tablets, PCs etc.) It’s vital to have the right technology in place to protect your devices from the latest threats and stop cyber criminals from gaining access to your data.
- Managed Antivirus – Proactively scan and silently remove viruses from devices, without slowing them down
- Managed Malware Protection – All internet traffic is filtered against malicious attacks and redirection
- Auto-deployment – Proactive installation of security services and policies on all devices
- Managed Device Encryption – Data on devices is protected with encryption
- Compliance Reporting – Compliance dashboard gives real time visibility on the status of security policies
- Mobile Device Policy Enforcement – Enforce strict controls on mobile devices to protect corporate data
- Managed Content Filtering – Filter content to ensure no inappropriate or malicious content is accessible through your network
- Managed Endpoint Control – Protect against infections, theft and data breach by managing and controlling USB ports
- Endpoint Alerting – Identifies and remediates non compliances on devices
- Web Security Reporting – Insights you need to further improve your cyber security strategy and reduce the risk of cyber-attack

Email Security
Prevent cyber criminals from using the latest spam, malware, and phishing techniques to access your email services.
Learn More
Cyber criminals often manipulate email services to access your data, carrying out attacks using spam, malware, and phishing techniques. It’s therefore crucial that you have the right measures in place to protect any data used in email communication, preventing data loss, unauthorised access, or compromise.
- Email Security – Keep emails safe from malware, spam and phishing attacks
- Email Anti-Impersonation – Prevent attacks from emails impersonating a trusted individual to gain access to money or data
- Email Backup – Back up email platforms such as Microsoft 365 so data is easily retrievable in event of data loss
- Email Link Protection – Validate link security when a user clicks on a link, preventing visiting phishing and malware sites
- Email Archiving – Store your old emails in a secure environment, which can be easily searched and audited when needed
- Secure Email Sending: SPF/ DKIM – Define which IP addresses can send email on your behalf and ensure emails aren’t altered in transit
- Microsoft 365 Security Audit – Review administrators, forwarding rules and users to maintain security, privacy and compliance

Employee Security
People are the weakest link in an organisation’s security. Train your staff to recognise potential threats.
Learn More
People are the weakest link in an organisation’s security. So, it’s crucial your staff are trained to recognise potential threats quickly and deal with them effectively. Moreover, it’s key that provisions are put in place regarding all passwords and data access to further prevent valuable personal or financial data from being stolen.
- Security Awareness Phishing – Spoof phishing emails are sent to employees at random times to test their ability to spot attacks
- Security Awareness Training – Educate your employees on cybersecurity best practices and pitfalls via interactive web training
- Password Management System – Store, share and create secure passwords in an encrypted vault to enhance productivity and security
- Password Policy Enforcement and Lock Out – Protect your business by enforcing a robust password policy across the company
- Dark Web Monitoring and Alerting – Continuously scans the Dark Web for your credentials and alerts and remediates if a breach occurs
- Multi-Factor Authentication – An additional layer of security to verify the identity of users before granting access to applications
- Device Access Insight – Find out which platforms, devices and browsers your team are using to access applications
- Password Strength Reporting – Identify weak passwords and take action to protect against cyber attack

Data Governance
Understand Your Data and Govern it to Mitigate Compliance Risks
Learn More
We deliver Data Classification and Governance consultancy services based on international framework and compliances.
The deliverables will involve:
- Assessment on how the information within the processing operation is collected, stored, used and deleted.
- Analyzing current data classification policy and finding the potential gaps
- Validation of data protection, data encryption, and storage mechanisms
- Catalog the range of threats and their related vulnerabilities, to the rights and freedoms of individuals whose data you collect and/or process.

ISO Consultancy
We deliver ISO 27001, ISO 22301, ISO 22301 Compliance services.
Learn More
The deliverables will involve:
- Gap Analysis against the ISO standards
- Gap Fulfilment
- Framework and Documentation Development
- Internal Audit.
FREE REPORT REVEALS
Don’t Trust Your Company’s Critical Data And Operations To Just Anyone!
Business Advisory Guide will arm you with 21 Revealing Questions you should ask any IT support company In Dubai before giving them access to your company’s network & data

THE BURHANI ADVANTAGE
Recognized as amongst the Top 1% of Microsoft Partners Worldwide
As a Microsoft Gold Partner with 20+ Years Experience, Burhani's Unique Mix of People, Process & Technology Enables Businesses Accelerate Digital Transformation by Leveraging the Power of the Microsoft Cloud
FREQUENTLY ASKED QUESTIONS
Managed Security Services FAQs
Frequently asked questions about cyber security posture improvement
What is a Managed Security Service?
A managed security service is a service designed to help organisations improve or augment their cyber security capabilities.
There are many different types of managed security service, each often focused around the management and monitoring of particularly security technologies, such as SIEM, EDR and vulnerability scanning tools.
Managed security service providers also conduct security audits, help organisations meet compliance requirements, and support incident response.
What is the difference between MSP and MSSP?
An MSP is a managed service provider and an MSSP is a managed security service provider. An MSP helps organisations with the day-to-day management and maintenance of IT systems and services, whereas an MSSP is focused on supporting security operations. Some MSPs offer managed security services but given the requirement for specialist skills and expertise in cyber security, many MSPs choose to work directly with MSSPs.
What are the Benefits of Managed Security Services?
By choosing to procure a managed security service, organisations that either lack sufficient security resources or need help to enhance operations can quickly elevate their cyber security maturity without the need to recruit and train a team of security professionals to work in-house. Use of managed security services can also result in significant cost savings in areas such staffing and training. Organisations can also outsource the time-consuming and onerous task of managing and monitoring security monitoring technologies, thereby enabling in house staff to focus on other priorities, increasing efficiency and reducing alert fatigue.
What is a Managed SOC Service?
A managed SOC service is a form of managed security service that provides organisations with an outsourced Security Operations Centre (SOC) – the facility that houses a team of security experts responsible for maintaining and improving an organisation’s cyber security. Outsourced SOC services help organisations build the ability to prevent, detect and respond to cyber threats.
How much does a Managed Security Service Cost?
The cost of a managed security service can vary significantly and is based on a wide range of factors, such as environment size, assets to be monitored, technologies deployed and managed, and service levels required. Managed security services tend to be subscription-based and significantly more cost-effective than equivalent investment in house.
RESOURCES
Managed Security Insights
Elevate Your Cyber Security Maturity with Useful Tips
GLOBAL PRESENCE. LOCAL SERVICE
Celebrating 20+ Years of Award-Winning IT Service Excellence